#how to check keylogger on windows
Explore tagged Tumblr posts
Text
“All I can really tell myself is that at least I’m not hurting anyone, as long as she never finds out. Which she never will. I’m careful. I have to be careful, to protect my lovely girl’s peace of mind from a creep like me.”
Summary: The internal monologue of a surprisingly self-aware stalker. But will that self-awareness be enough to save the object of their obsession?

Contains: cyberstalking, traditional stalking, obsessive thoughts, vague references to depression, discussion of/credible threat of kidnapping (no violence occurs).
Dipping my toe into sharing my original fiction. I do love a good guilt-ridden yandere.

She never looks around much when she’s walking to work. Probably because she’s too busy walking with a swagger, practically sauntering to the music playing through her earbuds. I’m too far back to hear, but I know she must have it blasting at full volume. She always does. When it’s raining and her roommate drives her to work, she has the radio up loud enough to shake the car windows. My girl–no, the girl, she’s not mine, keep it together–doesn’t do many things in silence. God, I love her for it.
But anyway. It’s a ritual: the most beautiful girl in the world leaves her apartment to go to work every afternoon at 2:45. I was never very punctual before I knew her, but somehow time doesn’t slip by in a haze anymore the way it used to. Each day is a discrete and individual thing to me now, because each day Kiara Martell leaves her apartment at 2:45 and walks to work.
And, yes, I follow her. At a discreet distance. I know it’s creepy. I know it’s wrong and disrespectful and would probably scare her if she ever found out. I know all of that, and I do it anyway. I can’t justify it, and I won’t try. Being honest with myself is kind of the only principle I have left.
All I can really tell myself is that at least I’m not hurting anyone, as long as she never finds out. Which she never will. I’m careful. I have to be careful, to protect my lovely girl’s peace of mind from a creep like me.
Today she’s walking with a slow, easy stride that I’ll admit drives me crazy. I pull out my phone, check the app: her phone is playing that old blues band again, the one she loves so much. No wonder she’s smiling like that, no wonder she’s tapping her left hand against her thigh as she walks.
Her nails match her bright yellow tank top. She’s adorable.
It’s a hot day today, and sweat glistens on her bare shoulder blades. It’s incredibly attractive, but also, is my girl wearing sunscreen? Should she be wearing a cover-up or something? One of those silky little vintage shawls she likes? I know she doesn’t wear sunscreen very often, the bottle has been lying in the exact same position on her dresser for weeks.
Do you see why I have to do this? No, not have to. I can’t ever let myself think that way. But do you see why I choose to do this? Why I return to the shadowy area in the corner of her apartment building’s parking lot like a sucker or a stalker, every day, by 2:40 at the latest?
Every detail of Kiara Martell’s life fascinates me. She is beautiful, but it isn’t just that. I know almost every detail of her life by now, and everything I learn just attracts me more. Her silly habits, her favorite shows, her messy bedroom but meticulously-organized music library, the way she hates her job but always greets her coworkers with a smile anyway… She’s just wonderful. She’s just perfect. That’s why I have to follow her like this, why I have to track her phone and read her texts with a keylogger and break into her apartment whenever I know no one’s home and spend an hour standing in front of her closet before I can talk myself out of stealing something, have to see and touch every part of her life, I have to, I have to, because how else am I supposed to prove to myself that she’s really real?
No woman has made me feel like this before. I didn’t know I was capable of feeling so much. It’s pathetic but it’s true: my life was empty before I knew her. My love for her (no, be honest: my obsession) gives me a reason to get up instead of lying in bed all day watching the ceiling fan revolve. Just by existing, she’s done so much for me. I just wish there was something, anything, I could do for her in return.
But I can’t think like that. I can’t let myself dwell on the money problems I could alleviate, or the home I could provide for her, or how I know she hates doing the dishes and I wouldn’t mind doing them every night. Because when I let myself think like that, my most dangerous fantasies start to sound way too plausible. When I let myself think about giving her anything, doing anything for her, I start thinking about how much more I could do for her if she just… came to live with me.
It wouldn’t have to be a kidnapping. In my fantasies (most of my fantasies, at least), she comes willingly. But that’s what makes daydreaming so dangerous: it always seems to gloss over the complicated details, and my mind skips straight to the part where the most wonderful woman in the world just happens to be fine with moving in with her deranged stalker. Totally comfortable with the whole situation, in fact. Jesus fucking Christ. I should get a therapist or something.
We’re almost there now, only two blocks away from the hotel where she works. In about five minutes, she’ll be covering up her cute, colorful clothes with the scratchy gray receptionist uniform that she always complains about in texts to her friends. I’ll sit in the cafe across the street, working or at least pretending to. And if I have to answer an email from a particularly annoying client, I’ll reward myself afterwards by letting myself watch Kiara for thirty seconds or so, while she sits at the front desk pretending not to be playing Scrabble on her phone. By now I’m very good at pretending that I’m just staring absently into space. I know sitting in plain sight by the window at the cafe is a risk, but I just can’t help myself.
And what happens next? Well, at about 9:00, or maybe 9:05, she’ll clock out and I’ll see her leaving the building. I will make myself wait, make myself move slowly as I pack up my laptop and bus my empty coffee cup, so that she won’t see me following her in the shadows as she slowly walks home. She’ll be swinging her empty water bottle in one hand, and she’ll have earbuds in again, which is the only thing she does that genuinely pisses me off. It’s not safe! A woman walking home alone at night needs to pay attention to her surroundings. Doesn’t she know what kind of weirdos are out there, in a big city like this?
Well, I guess it’s probably better for me if she doesn’t know. But still.
At least she isn’t ever really alone.
You know, there’s this one part of my girl’s walk home that always drives me a little crazy. There’s a little park, with a playground and big, leafy trees, that she always cuts through to shave a few minutes off her commute. It’s fine during the day, because during the day it’s light out. There’s plenty of people there during the day, mostly cute little kids playing on the playground while their parents watch.
But at night… at night the park is always deserted. And dark, very dark, because the city never bothered to put up safety lighting here, and those tall trees blot out even the moon. And there’s Kiara, cutting through this park every night. Alone. With her earbuds in. And it drives me crazy, because even if I would never do it, even though I could never hurt or scare her like that, not after everything she’s done for me without even knowing it, even though I don’t really mean it, even still, even still, even still, part of me always thinks: if I was going to kidnap–no, take her home with me, it would be so easy to do it right now.
But I wouldn’t do it. Really, I wouldn’t.
Even if I do think about it all the time now. Even if it’s harder and harder to think about anything else.
I really should get a therapist.
#yandere#yandere x darling#yandere fiction#yandere oc#op#kiara#<-just in case i ever write about this couple again#just a kid in love :) just a super normal kid in love :)
17 notes
·
View notes
Text
Knowledge
For @amonthofwhump 12 Days of Whumpmas, Day 2: Krampus
Sensory Overload | Temptation | Whipping | Comfort: Decorating Cookies
Death Valley on AO3
CW: Past trauma, dissociative state, references to Noah's gaslighting and emotional abuse
-
Somewhere in Illinois, Present Day
It was a perfectly normal place to park his truck between jobs, while driving to the next meetup point. Nothing suspicious at all about choosing to stop here, in this tiny little town in the middle of nowhere. No reason for Noah to call, check into his phone, look at the keylogger on his laptop, or start digging through the scraps of a life Finn Schneider had - however painstakingly - built.
No reason for Noah to even think twice.
Even though he knew, he knew Noah would think about him. Would look at the location on the GPS tracker in the truck and see if the phone and the laptop matched up. See if there was any activity. Look at what Finn searched for, what keywords he might use.
Noah always knew everything.
Not this, though.
At least... not yet.
The man who had once been called Finn Schneider stared through the windshield of his truck into the diner that took up half of the enormous truck stop, settled snugly against an interstate highway with another, smaller country highway intersecting. Through the windows, a few booths held lonely truck drivers with eyes glued to a football game playing on a television up on the wall. A gaggle of teenagers giggled over shared plates of french fries and cups of weak coffee doused in enough creamer to turn it nearly white. A man with two small children watched with a tired smile as the kids gestured wildly.
On the interstate, traffic roared by - people heading home to their families after a long work day, as the sun began to set.
Here Finn sat.
His heart was in his throat, his knuckles white where he was still gripping the wheel. Beside him on the front seat, Little Mother yawned, her teeth clicking when her mouth shut, and slowly blinked at him. In the back of the cab, the kittens were playing with the catnip mice and other toys he’d bought for them. One made mincemeat of a stuffed penguin, casually ripping the stuffing out of with a predator’s zeal for a satisfied hunt.
He could do two things, right now.
He could walk inside, order dinner at the diner, have a shower in the facilities along the back, call Noah, sit and eat, and then head back into the truck to watch a movie and sleep. It would be the safe thing to do - what Noah expected him to do. What he always did, at the end of a day driving to his next task.
Call Noah, get the details on the next job, and keep living how he had been for so long, for almost two decades.
But... there was one other thing he could do, as well.
Riskier.
Not safe.
Noah could find out what he was up to, know that Finn had… doubts. Worries. That he wasn't sure what was real. He didn’t know what would happen, if Noah knew that there were things he said that Finn didn’t really believe any longer. Probably he’d just… talk to him, like he did sometimes. An arm slung over his shoulder, a hand rubbing his back, close enough to his face to make Finn tense with the memory of another man's diesel smell.
Noah would explain with casual certainty that the truth was a version of reality that didn’t quite match the one seen through Finn’s eyes.
But then, he couldn’t trust his eyes, his mind. Not anymore. Not since Robert. His mind invented shadows, his eyes saw shimmers of the bones in the basement, the bars of his cage. His reality was laced around every edge with too much darkness.
But...
That didn't mean Noah's reality was true.
How long he sat there, arguing with himself, he wasn't sure. People walked into the diner or out of it, laughing and joking, bundled up against the harsh winter chill. The teenagers left. Some truck drivers left, while others headed inside for their turn at hot showers and hot food, sometimes giving Finn a sidelong wave, thinking he was one of them.
He was.
Sort of.
Was he?
He felt like Adam and Eve, weighing the fruit of the tree of knowledge, knowing he shouldn’t take it. Holding it heavy in one hand, while the serpent whispered Ihr werdet mitnichten des Todes sterben... What if Noah was angry with him, for looking? What if he found nothing, only his own madness?
What if Noah was right, that he had lost his mind in Robert's house, that he could never reclaim it?
But... Noah lied.
Finn was more sure of it with each passing year. He couldn't trust his own mind, his own eyes, his own heartbeat, but... he could trust documentation, he could trust words written down, records... maybe Noah would be angry, but the idea of not knowing was an agony worse than whatever the knowledge he discovered might be.
Wasn’t it?
Finn must have left his own mind again, too lost in trying to decide if he wanted to know the truth or not, if he wanted to take a bite of the apple from the serpent’s hands. Or was Noah the serpent?
Somewhere in his panic, his mind and body must have split apart into two halves. It had happened before. His body went around doing things while his mind was locked in a cycle of thoughts he couldn't pull himself away from.
It was why Noah said he couldn’t be left alone, needed to be tracked. Sometimes he left his body, and stopped answering the phone.
He blinked.
The next time Finn was aware of himself, he wasn't in the truck. He wasn't in the diner, either.
Instead, he found himself walking past a water tower, halfway across the length of the tiny little town, crossing railroad tracks with the wind pushing against his back.
His hands were in his coat pockets - his body had put on his coat, apparently - and his face burned from the biting freeze of air around him. He’d pulled a knit cap down over his head, which he couldn’t remember doing, either. His cell phone wasn’t in his pocket, and his heart skipped and then picked up speed again.
He came to a stop so sudden his boots scraped on gravel along the side of the road, staring straight ahead.
He must have left it in the truck.
Noah would-
Maybe not know.
If he didn't call, he wouldn't know.
Right?
Someone drove past, slowed their truck down, watched him. It was a town small enough that even a single stranger walking through the tiny town square was noticed. His hometown had been small, a little like that, although not this small. His mother would have slowed her car down, known every cousin visiting family, every boyfriend or girlfriend meeting someone’s parents for the first time.
The town square was more of an oblong oval shape, vaguely uneven on one side. To his right, two big grain silos rose two stories high, gleaming metal that blinded him when the setting sun bounced off the exterior. To his left, old brick buildings that seemed to lean on each other for support, places that had once been a grocery store, some kind of antique shop now maybe. In front of one, where the brick had seen better days and some of it lay crumbled on the sidewalk, was a strange, incongruously gorgeous red sports car.
That building had a light on upstairs. He could see a man on an exercise bike through the window, watching a TV.
Finn headed straight across the road, passing through a small park in the center of the town square that was only big enough to hold a picnic area, two large trees - one decorated for Christmas - and a single stone bench.
In front of him now, there was a post office, the town library, and what seemed like a combination bank, place to pay utility bills, and… town hall. He frowned, the expression faint and barely-there, wondering what he was doing here.
There was nothing in this town. Nothing to it.
What was he doing?
Then his gaze went back to the library, the entire inside warmly lit against the outside chill. He could look right in and see a woman with two small children encouraging them to look at a bookshelf, a toddler playing at a table full of legos while her mother sipped something from a paper cup, the librarian moving one pile of books from one table to another with patient certainty.
Then, all at once, Finn understood what he was looking for:
A computer.
An old desktop,squatting on a folding table as if it were merely an afterthought, someone’s donated castoff. But the screen was on, the chair in front of it was empty, and Finn knew what he wanted to do, how he could keep Noah from knowing he'd done it.
He walked inside, steeling himself for the way all three women stared at him openly, without even trying to hide it. The weight of their gaze prickled on his skin; he was far more used to being ignored or going unnoticed.
“Welcome in,” The librarian said, in a tone somewhere between baffled and amused. “What can we help you with tonight?”
“I would like to use your computer,” Finn said, and pretended he didn’t see the sudden burst of interest in the faces of the women with children here, who glanced at each other when they heard his accent. “Mine is-... mine is broken.”
Why he bothered with the lie, answering a question she hadn’t asked, was beyond him. His heart beat so fast and so hard he was sure he must sound out of breath.
But she smiled, nodding knowingly. “Of course. You must be one of Bob Kaufmann’s cousins in for Greta’s hundredth, huh?”
Finn leaped on the excuse. He’d be gone in a few hours. No one would ever need to know. “Ah, yes, I am. How did you know?” He managed a grin, and the librarian laughed. She didn’t see it wasn’t real, was simply painted-on. He never smiled and meant it, unless it was for Little Mother or the kittens. Not anymore.
“Well, you know. There were some signs that you might not be local to the area,” She replied, dry as a bone, and he huffed a laugh - surprised to hear it, and realize it had come from him.
“I see. You don’t mind if I use the computer?”
“Oh, not at all. It’s got a sixty-minute limit and then it’ll kick you out, but just let me know and I’ll let you back in.” She waved a hand and went back to her work, and he nodded, moving through the small space packed with bookshelves on every side until he made it to the computer chair and took a seat.
It didn’t take the full hour.
He didn’t know Noah’s real name, but he knew the phone number his wife called him from, searched for where the area code for that number was located.
He also knew Noah’s license plate number. Then he started looking, city by city in the state the license plate was from, at vehicle registration lists.
The third city he searched within the area code popped up a name.
Searching for house taxes using that name gave him an address, he owned a home in a cul-de-sac, he owned three other cars besides the truck. There was a second homeowner listed on his house taxes.
Edward Paulson. Wife - Christina Paulson. Finn looked her up by name and city, found a nurse by her name listed as working at a hospital there. She had a facebook, an instagram, and on the facebook were pictures of the same woman, two young boys, and… Noah.
Smiling, an arm around her shoulders just like he did with Finn sometimes. Another photo with a hand to her lower back.
Did he rub her back, when she was scared? Tell her things weren't the way she thought, that she couldn't trust her own eyes?
Did she know about Finn?
He asked politely for a piece of paper and a pen, a noise like static rising in his mind.
When he made it back to his truck, a harsh wind had risen and his nose and cheekbones felt cut to ribbons by the freeze. Little Mother greeted him with a cheerful chirp, and he rubbed a hand over the perfect soft round curve of her head, his other hand holding onto the names and address he had written down folded inside his pocket, while he stared at what he had done but did not remember doing before he left the truck.
Sometime between the temptation and taking action, he had set up his laptop to play a movie. There was a fight scene, tinny voices shouting. His phone was charging beside it. If Noah checked, he would see what movie was playing. He would think Finn had not left the truck.
Unless he'd called and Finn hadn't answered.
Panic thrilled through him again, but there was no missed call. Noah hadn't tried to talk to him. He could still call him later, pretend everything was normal.
That he wasn't-
That Finn wasn't giving in to his doubts.
For a while, he sat and stared again, willing the static noise in his mind to soften, so he could hear himself think again. Then he took a deep breath and grabbed his backpack.
He headed in to get a shower and some food, taking his phone with him this time so Noah would see that when the movie finished, he headed into the diner.
Normal night.
Perfectly normal.
He would go to sleep early tonight.
He had a long, long drive to make tomorrow.
-
@whumperfully@pigeonwhumps @squishablesunbeam @darkthingshappen @whumper-soot @pumpkin-spice-whump @pardonmekreature @d-cs @whump-queen @sowhumpful
#amow day 2#amow#12 days of whumpmas#temptation#traumatized whumpee#dissociated whumpee#referenced gaslighting#psychological whump#emotional whump#whump#death valley fic#finn schneider
53 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
extremely long post below the cut, please read the entire thing b4 brashly doing anything. there's a lot and there is scaling difficulty with the steps you can take.
it's actually better for android users to debloat their phones than to just turn off settings — if done correctly, you're able to fully uninstall apps from your phone.
we already know that, after Facebook being put on trial in 2012 (settled in 2022 for a measely $90m out of their $590b) due to their tracking settings — even if off — are still running. even if you turn phone settings off, apps are able to "see" one another and collect data that way. including your keyboard. i repeat:
YOUR PRE-INSTALLED PHONE KEYBOARD IS A DATA COLLECTOR
the issue is that debloating your phone takes a little know-how, and you need a PC to do it. you cannot just "disable" apps from your phone, they're still functional at some capacity.
i REALLY recommend using UAD (Universal Android Debloater) if possible. which, again, requires a computer — i also recommend that you entirely stop using any and all Google services. i am talking down to: Learning How to Read A Map
no more google maps. yes, it's a total pain in the ass, but data collection is not a joke. gmail is a data collector, YouTube is a data collector any form of docs/sheets is a collector, and again:
i cannot fucking stress this enough.
YOUR PRE-INSTALLED KEYBOARD COLLECTS YOUR KEYSTROKE DATA.
IT. TRACKS. WHAT. YOU. ARE. TYPING.
this link has installation instructions for UAD — this is to debloat your phone, focusing on unnecessary Samsung and Google apps. the major 2 problems are: you will need a computer, and you will need to learn how to use GitHub thru YT tutorials.
learning how to use GitHub will be extremely important for protecting your PC as well from Windows bullshit
🗣️DO THIS FIFTH🗣️
a chart of what apps to uninstall and what they do:
(there are also some other ways to stop/uninstall apps on this post, but i don't know the details behind them and recommend you look into them yourself if you can't use UAD)
🗣️DO THIS FOURTH🗣️
for a Google Play Store replacement:
list of games available on fdroid:
🗣️DO THIS FIRST🗣️
for a non-tracking QWERTY, QWERTZ, AZERTY, Kurdish QWERTY, Russian, and more keyboard:
for a non-tracking Japanese 3x4 keyboard:
🗣️DO THIS SECOND🗣️
NewPipe is the YT alternative; this app prevents Google from collecting your IP and you no longer have 1) ads 2) to login 3) afk prompts to check if "you're still there".
🗣️DO THIS THIRD🗣️
USE FIREFOX AND TOR. set your default search engine to DuckDuckGo on FF
(there's actually discussion on whether or not firefox is completely trustworthy on mobile due to their code not being entirely opensource. something to do with working with google. the f-droid alternative is Fennec)
also please read a bit about how to properly use Tor; the tldr is to not login to anything — social media, emails, news sites — while using it
an endnote:
you do NOT have to do this all at once; i started out with swapping my keyboard and YT over first. i'd recommend at least doing your keyboard.
i just recently swapped to fdroid and installed Tor. i'm currently swapping out all of my gmail accounts for protonmail, tutamail, and mailfence.
i haven't even opened UAD yet, as i'm still in the process of finding app equivalents on fdroid and untangling myself from google services.
these will ALL take time getting used to — it sucks and the keyboards are absolutely not as efficient, but that's because there are no installed keyloggers. do not let laziness borne out of ease of use from proprietary apps and software prevent you from protecting yourself. i cannot stress this enough : do not be lazy about this.
r/privacy, r/cybersecurity, and privacyguides are great places to get started in understanding how to protect yourself online. i definitely recommend you start looking into how to do so on your PC as well, if you've got one
as for iOS users?
you're shit outta luck.



anyway yeah DELETE YOUR FUCKING ADVERTISING IDS
Android:
Settings ➡️ Google ➡️ all services ➡️ Ads ➡️ Delete advertising ID
(may differ slightly depending on android version and manufacturer firmware. you can't just search settings for "advertising ID" of course 🔪)
iOS:
Settings ➡️ privacy ➡️ tracking ➡️ toggle "allow apps to request to track" to OFF
and ALSO settings ➡️ privacy ➡️ Apple advertising ➡️ toggle "personalized ads" to OFF
more details about the process here via the EFF
#data privacy#online privacy#such a long post…#politics#? is it politics idk#iOS is entirely proprietary and closed source‚ that's why you're unable to do anything that android/samsung can do#i personally plan on getting a phone where i can swap the entire OS out but that'll be down the line
44K notes
·
View notes
Photo

Check the detailed guide and easiest way on how to detect keyloggers that are installed and hidden in your Windows PC along with their types, some preventive measures to get rid off and secure your Computer
#5 Ways To Check For Keylogger On Windows Computer#ways to check for keylogger on windows computer#how to check keylogger on windows
1 note
·
View note
Text
New Discord malware attack
pretty much what the title says. There’s currently a new socially engineered malware attack on Discord since possible around July, and currently it is vicious. I’ll make a brief explanation of what it is, what to do if you click on the link and a measure me and some friends have done.
What it is
A direct message from a friend (currently) talking about checking out the game they're working on. The typing style may look very similar to what they actually talk like. What clicking on the link does is steal your account, install a downloader (most likely a crypto miner), a keylogger, harvest logins from all your browsers and possibly something else since this is very new. While its a simple “don’t click any suspicious links” advice since the start of the internet, I’m making this for those that are unaware.
here’s an analysis of what it does:

[ID: Doing some analysis now, it's absurd, the thing BROKE MY DEBUGGER, it got a lot of weird misplaced bytes in the exe header and a tentative of buffer overflow that didn't work thankfully because I was in linux, so the kernel just crashed -.- This thing is a Node Executable as front, have a token stealer, have code to break into passwords kepts in lots of places of your OS (covers every browser), it also monitors your network, hooks NtOpenKey, WSASend, WSARrecv, AND EVEN CREATEPROCESS. Oh yeah, it also hooks to your key inputs, so call it a keylogger too. It's designed to break debuggers and try to f*ck with you... from inside the debugger, without executing it. It's a complete Security Stealing Ware. Didn't find anything that could point tentatives to mess with your bios/firmware (in these cases, even reinstalling the OS may not be secure enough lol) I still can't believe a virus just tried to do with me, what I try to do with the Switch and PS4 on my spare time lol. end ID]
What to do if you click on the link
this screenshot (and entire post) is from twitter user @/PhleBuster and it goes in detail on what to do if you actually click the link.
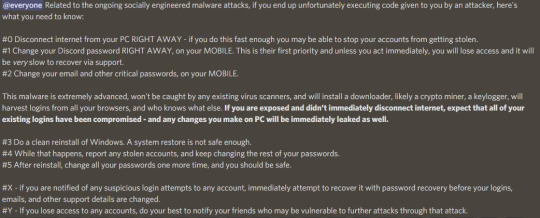
[ID: @everyone Related to the ongoing socially engineered malware attacks, if you end up unfortunately executing code given to you by an attacker, here's what you need to know: #0 Disconnect internet from your PC RIGHT AWAY - if you do this fast enough you may be able to stop your accounts from getting stolen. #1 Change your Discord password RIGHT AWAY, on your MOBILE. This is their first priority and unless you act immediately, you will lose access and it will be very slow to recover via support. #2 Change your email and other critical passwords, on your MOBILE. This malware is extremely advanced, won't be caught by any existing virus scanners, and will install a downloader, likely a crypto miner, a keylogger, will harvest logins from all your browsers, and who knows what else. [in bold:] If you are exposed and didn't immediately disconnect internet, expect that all of your existing logins have been compromised - and any changes you make on PC will be immediately leaked as well. [normal font:] #3 Do a clean reinstall of Windows. A system restore is not safe enough. #4 While that happens, report any stolen accounts, and keep changing the rest of your passwords. #5 After reinstall, change all your passwords one more time, and you should be safe. #X - if you are notified of any suspicious login attempts to any account, immediately attempt to recover it with password recovery before your logins, emails, and other support details are changed. #Y - If you lose access to any accounts, do your best to notify your friends who may be vulnerable to further attacks through that attack. ID end]
Prevention between friends
Since this is still relatively a new attack, please take this part with a big grain of salt. Me and my friends made a system for our own group of sending a personalized message between a spoiler filter before sending links. I’m not sure how the hacked message is supposed to look since from my own research, it just looks like your regular spam message. Try to figure out a 2FA system with your friends on what links are trustworthy. While it is currently a “hey check out my game” type of message, it worries me that it might spread to other types of links.
I’ll try to update this if any new information arises, but please stay wary of any links being sent on discord. Stay safe
#sorry for this being so long i just ahvent seen any post on this on tumblr#me being paranoid doesnt help this at all but im trying to stay safe#discord#discord messaging#out of context discord
5 notes
·
View notes
Text
Safe Torrent Downloader

Our BitTorrent Web and Classic products for Windows are available in one location to help you quickly find the version that suits you. Download today. Apr 17, 2020. BitTorrent is a peer-to-peer communications protocol for efficiently sending any type of file, large or small, over the Internet. Safe torrenting software, such as such as BitTorrent Classic, are needed to send or receive files using the protocol.
uTorrent is the most popular torrent client in the world by a large margin, but is uTorrent safe? This guide will teach you how to use uTorrent as safely as possible, and how to get the most from your uTorrent experience.
Cached
You’ll learn:
What safety issues does uTorrent have?
The safest versions of uTorrent to use (and which ones contain malware)
How to block ads in uTorrent
How to protect your identity when downloading torrents with uTorrent
We recommend you also read:
How to use uTorrent anonymously (Learn to hide your uTorrent IP address and encrypt your torrents)
uTorrent proxy setup instructions (use a SOCKS proxy for more anonymous downloads)
QUESTIONS ABOUT UTORRENT’S SAFETY
uTorrent made news across the internet in 2015 when it was reported that they were bundling bitcoin mining software that would auto-install along with uTorrent and secretly use host machines to mine for bitcoins without the users’ knowledge.
It turns out that this issue wasn’t widespread, and uTorrent removed the malware from future releases, but it did raise questions about how far the company is willing to go in order to generate revenue. Currently, the bulk of their revenue comes from low-cost advertising and the small percentage of users who choose to upgrade to utorrent pro for $19.95/year.
In 2014, google’s chrome browser also flagged uTorrent software as malware though it came up clean on virus scanners. This issue was temporary as well and likely had nothing to do with the actual risk of installing the software.
Adware and ransomeware bundled with other torrent clients, has demonstrated the risk of installing torrent software, even from reputable sources. In March 2016, an update of Transmission torrent client (distributed from the company’s own servers) was infected with ransomeware which would hold users’ systems hostage by encrypting the harddisk and demanding a ransom payment in bitcoins.
SO IS IT SAFE TO USE UTORRENT?
The short answer is yes, but it’s complicated.
Currently, uTorrent’s software is considered safe and free of dangerous malware. The primary risk of using uTorrent comes not from the software itself, but the risk of downloading dangerous or infected torrents from unknown sources. No torrent client can protect you if you choose to download unsafe files which may contain rootkits, malware, or trojans. Read our safe torrent guide for our top prevention/safety tips.
It’s also a good idea to always your identity when downloading torrents, and to encrypt your traffic so you can’t be blocked or throttled by your internet provider. We wrote our‘ultimate guide to anonymous utorrent’ to show you exactly how to hide your identity while torrenting.
Safest versions of uTorrent
There is great debate over the best version of uTorrent released over the years. Some versions are more stable then others (and have less privacy leaking features). Over time, uTorrent has become much more bloated (with extra features) and less lightweight then it was in the early days.
Among hardcore veterans, uTorrent version 2.2.1 is still the favorite (and considered the last version not bundled with adware). You can still find download links to this old utorrent version (though always software from unknown sources before installing. This reddit thread has several links to download this OG version.
Save Torrent Downloader
You can also find previous versions of uTorrent on oldversion.com
USING UTORRENT ANONYMOUSLY
We always recommend taking steps to hide and anonymize your torrent downloads. By using a VPN (best option) and/or a proxy service, you can make your torrent downloads virtually impossible to monitor or trace.
Here are some step-by-step guides to help you use utorrent safely:
How to use uTorrent Anonymously (VPN + Proxy setup instructions)
You will also likely find this youtube video helpful. It includes step by step instructions showing you how to use a VPN or Proxy with uTorrent, and how to check your torrent IP address to verify your setup is working and your IP is hidden.
10 Best Free Torrent Clients For Downloading Torrents (2020)
HOW TO REMOVE ADS FROM UTORRENT
Advertisements in uTorrent can be rather annoying. Fortunately, you can choose to disable them by tweaking a few advanced settings in the uTorrent preferences menu.
Ubergizmo has the complete guide on how to disable ads in uTorrent.
Safe Torrent Downloader
Best of all, this isn’t some hack method. It’s actually a built in option buried deep in the uTorrent’s menu. It works great, and you can have an ad-free uTorrent experience in just a few minutes.
FINAL THOUGHTS
uTorrent is still the torrent client of choice for over 100 million users worldwide. The software itself remains relatively safe, though if you want a true ad-free and adware-less torrent experience, you should consider trying one of the open-source torrent clients like Deluge or Qbittorrent, both of which are extremely functional and popular.
The biggest risk with uTorrent (and with any torrent software) is what you download, and where you download it from. The safest practice is to never download installable files or software such as .EXE or .BAT files, which could contain dangerous software, keyloggers, spyware, etc. You should also have a high-quality antivirus, and use it frequently. Read our Safe Torrent Guide for a full list of good safety practices.
Be well, torrent safely and always use strong protection.
Ryan McCarthy
Safe Utorrent Download Windows 10
Ryan is the editor and head reviewer. He's been a tech geek and digital privacy enthusiast since the Y2k freakout in '99. When not writing BitTorrent tutorials, he can usually be found sipping a lager or playing pickup football (the real kind).

1 note
·
View note
Text
install webroot download windows 10
install webroot download windows 10- Activate Webroot antivirus in your PC, Andriod or Laptops and protects them from the virus, spam & malware.
How can webroot.com/safe help me?
Webroot support specialists can lend you their hands to download, install and update Webroot Spy Sweeper Antivirus on your system. We can also correct all errors that can crop up when installing and configuring Webroot Antivirus on your PC. We can help you detect and remove malicious threats, malware, and spyware by doing a quick scan of all files and folders. With our robust technology, we can delete suspicious programs and infected files from your system. Our antivirus specialists can clean up all online threats, including Trojans, rootkits, keyloggers, and worms. We can optimize the speed and efficiency of your computer and also prevent it from becoming sluggish.
And now just give us the green light to remotely access your computer via the Internet and our certified technicians can protect you from identity theft and prevent unauthorized users from accessing your computer and personal data.
Where to seek out webroot Key Code?
The Webroot security package is simple for you to set up and installs at www.webroot.com/safe. So just find a 20-character alpha-numeric code written on the back of the retail card. Then here is a sample product key to understanding you:xxxx-xxxx-xxxx-xxxx-xxxx
Welcome to install webroot secure anywhere with key code
Before you step ahead to install the software, confirm that you meet these conditions:
If you have an older version of Webroot antivirus on your System, either update it or reinstall it from the official website.
In case you have another antivirus, Uninstall it before downloading and installing Webroot safe as it might cause software conflicts and even affect a computer’s performance. Go to control panel/ settings to uninstall other antiviruses.
Make sure your computer has enough space to install the antivirus.
Before you purchase Webroot antivirus, it is essential to check for system specifications as you need to know which version of any Operating system supports a certain version of the antivirus.
If you already have been using Webroot antivirus, you simply need an upgrade and reactivate it.
install webroot download windows 10 Advantage for Businesses:
install webroot download windows 10 -Businesses require different multi-level protection as compared to private users. With smarter cyber protection, you can safeguard your employees and company with hassle multi-vector protection for desktops, laptops, virtual machines, tablets and smartphones with www.webroot.com safe especially home users. By providing Managed Service Providers with multi-vector security solutions, the Webroot Channel Edge Program promises recurring revenue, increased profitability, sales support and enablement tools. The brand’s cloud-based Threat Intelligence Services help to protect your customers with new unanticipated sophisticated online dangers. Read on to know the advantages that your business can enjoy with these services. You can try out each of these with free trials and choose the one that best suits your requirements to keep cyber threats at bay and gain complete control of your business. With Webroot Safe Install, you can protect your computers and devices.
Endpoint Protection – Endpoint protection is very crucial for every business computer and allied devices.
Countless mails have malicious attachments to phishing sites that serve as thriving ground for hackers, viruses and other malware. But if you secure your system with multi-vector protection, you can safeguard every endpoint across various users and prevent online attacks of all kinds.
Channel Edge MSP Program – This is designed to increase and improve the functioning of every business. Apart from protection you also get resources, flexible billing and easy management that is needed for flourishing your business by delivering superior services in every aspect.
Protection through Machine Learning – The Webroot Threat Intelligence platform is a cloud-based feature that aids every business with accuracy, context organizations and vendors that is needed to protect themselves as well as their customers across all online activities. Webroot Setup install helps you with antivirus installations.
1 note
·
View note
Text
How to hack Instagram Password online
In order to hinder your Instagram account from falling into a wrong hands, it is essential to find the hack instagram mystery expression quickly. For this, INSTALL PASS DECRYPTOR: Recollect that our item is used every day by a colossal number of customers that have lost their mystery key. In like manner large names are hacked. Julian Edelman for example, has been hacked in June 2019. The suitable reaction of the riddle question was the name of his better half. It was definitely not hard to hack his record.

There is an average system that developers all use to hack Instagram passwords. This is a phishing page where the developer will show an Instagram login page that will look exactly like the certified Instagram login page. As a general rule, they use the programming capacities and enormous spam email where they will send in an email containing the going with message "This individual has indicated your profile picture on Instagram, click here to check your photo", and once you have tapped on the association, you will be occupied to the fake login page. By then, when you have entered your mystery expression, it will be normally sent to the developer who sent you the fake login email. The fake page will by then change into a certified login page and you will be truly redirected to the genuine Instagram page. As a general rule, the harmed individual doesn't comprehend that his mystery key has been hacked.
This is one of the basic instruments used to get a tragic setback's passwords: the Keylogger. This is a tad of Instagram developer programming that fits into the system memory of your contraption and runs at each boot. These keyloggers record all of the keystrokes you type. A log is made with all of the letters you formed and is thusly sent to the developer. Ardamax Keylogger is one of the most acclaimed Keylogger. The customer can changed the methodology name with the objective that it can not be indicated when someone looks for it in the Windows Task Manager. This makes the task impressively progressively difficult to recognize and to clear it! In case you think you are starting at now a harmed individual, you should start by using a virtual comfort online when you type a mystery expression for unprecedented tricky goals, for instance, your record or your Instagram account.
Another theft gadget is: the RAT! Rat means "remote association device". A software engineer can interface with your PC without your consent with RAT. It can see what happens on the screen, what you are doing at present, what goals you visit... A keylogger is moreover planned. The developer has the probability to copy all of the archives from your HDD to his contraption and this without you seeing it!
Exactly when you run the keygen or fix you will get what you need, anyway out of sight, your system will be spoiled with a dangerous Trojan. For example, Turkojan is a particularly used Trojan contamination. Having tainted an immense number of PCs on the planet. Understand that a Trojan is more predominant than keyloggers and RAT. It gives altogether progressively opportunity to software engineers to take your Instagram affirmations.
The system's overview is amazingly long, anyway the standard ones have been recorded beforehand. There are various ways that a developer will use. For example, if both are related with the Internet on an equal switch, a developer can use any key decoder to scrutinize all the sensitive data transmitted by your PC. This is one motivation behind why it is for each situation better to engage secure course at each conceivable chance.
Most areas like Instagram are altogether helpless against their customers and the proof is that you are progressively more reliably using our item PASS DECRYPTOR to find your lost mystery word! The approval methodology of this photo sharing application was agonizingly debilitated in control and affirmation limits, which made it easy to make savage force attacks. It's not in light of the fact that a help is standard that it is in like manner all around confirmed. Instagram for example, this photo sharing application, which as of now displays more than 1 billion customers around the globe, investigated get to security accounts. Starting late, a tremendous hack of Instagram passwords has been revealed on the web, there are no under 49 millions hacked accounts containing private information on the Internet and more is going up each hour.
1 note
·
View note
Text
How to throw out virus from a PC with Norton Antivirus Technical Support?
Antivirus programming that is the means by which we as a rule call the antivirus application or antimalware application, additionally abbreviated as AV, is overall the code that we use to recognize, stop and dispose of any malicious programming. Indeed, that is the fundamental meaning of antivirus.
The Norton antivirus is a famous security programming that was at first created to distinguish and dispose of PC infections, despite the fact that with different sorts of malware contaminations excessively assaulting, the norton.com/activate has been additionally altered, helping in the sticking of a wide range of pernicious assaults, together with ransomware, wholesale fraud, keyloggers, Trojan steeds, worms, rootkits, vindictive program, program criminals, malignant diallers, adware, spyware just as the extortion devices. These assaults are additionally reached out to noxious connections, spam messages, banking dangers on the web, online life fakes, propelled dangers, and DDoS dispatches. All these can be halted with direction from xfinity.com/norton.
After the Norton antivirus clarification, how about we currently talk about the other crucial thing, to be specific infection cancellation with comcast.com/norton Technical Support.
How to dispose of an infection from a PC with Norton Antivirus Technical Support?
There are various basic things that require to be put aside as a top priority as connection to taking out infection just as malignant application from a PC. How about we view that:
On the off chance that you accept your gadget could be assaulted, you need to distinguish the sort of assault. For this, you require to play out a profound output with your Norton Antivirus Activation Support. You can dispatch your norton.com/setup scanner by the direction of Windows notice or by Norton Antivirus Technical Support. The specialist there would play out a full gadget examine that encourages you distinguish all assaults on your machine.
Your www norton.com/ setup helps recognize the assaults and infection on your gadget. A notice will come after the Norton infection analyze, giving options to either move the infection to the infection box or evacuate the noxious information. You can choose whichever of the choice, to remain away of the malevolent assaults. There is additionally the option of calling Norton Antivirus Activation Support in the event that you don't have antivirus application introduced on your PC gadget.
norton.com/ setup Technical Support likewise pursues an infection check taking remote access of the client gadget. In the event that you accept your PC could be assaulted and if by any plausibility you don't contain an antivirus application in your PC, contact Norton Antivirus Technical Support. There are numerous online outsider specialized help supplier that would analyze your PC hard plate for covered up infections. Indeed, given that there are various choices to get a www norton.com/setup Activation Support, you would be advised to choose the suitable one.

Some helpful hints from Norton Antivirus Technical Support:-
Manual uncovering and expulsion of malware infections isn't recommended by specialists. This is for the explanation that you may wind up expelling the inaccurate driver records, which continuously could cause specialized mistakes on your machine or make your Operating System to go undermined.
There are a great deal of models when you get it's an infection danger that has lead specialized issues with your gadget while as a general rule it's most certainly not. It may even now be an issue associated with programming, system, driver, or applications. Accordingly on the off chance that you are encountering a specialized issue and the profound sweep utilizing the norton.com/setup download programming uncovers that no contaminations have been recognized, you may initially comfort yourself by approaching the Norton Antivirus Activation Support online output with antimalware application.
Extent of Norton Antivirus Technical Support:-
Norton Antivirus Technical Support for Rootkits Scan.
Norton Antivirus Technical Support for cleaning rootkits.
Norton Antivirus Technical Support for following output.
Norton Antivirus Technical Support for checking of packed records, and a few more
Tags
norton.com/activate
norton.com/setup
norton.com/ setup
www norton.com/setup
www norton.com/ setup
norton.com/setup download
xfinity.com/norton
comcast.com/norton
1 note
·
View note
Text
Come Down


gif
Words: 1822
Characters: Willow Wren, Jessica Jones
Prompt/Tag: “Did I do something illegal? You bet I did! Was it fun though? Hell yeah!” x / @anti-solidcoffee
Summary: Willow pulls off a dangerous stunt and pays the consequences
Song: Goodbye Yellow Brick Road – Elton John, Jamie Bell, Taron Egarton
—————————————————————————–
I arrive at the scene of the incident just as police are, rolling up in a motorcade of blue and red lights. Okay, okay, what’s going on, what’s the scene, etcetera etcetera.
Two guys are bleeding out in the middle of the street, traffic is stopped, and cars have parked haphazardly around the scene. On my right, there’s a jewelry store with smashed windows. And then I spot two men stepping out of the busted-up store, and I hear the metallic click of a safety being turned off.
Oh, this could get messy really quickly.
Most people have gotten the hint to run, but others are still standing too close, phones out, recording.
“Shit, shit, shit,” I say and duck behind a closed newsstand. I pull my hood over my head, but my face is still visible. In my backpack, I find a pair of large sunglasses and white facepaint from school spirit day last week. “Fuck,” I say, and pop open the tube, smearing streaks of paint on my face before putting the sunglasses on. “Clown nation let’s rise.” It doesn’t cover my whole face but just obscures the rest of my features. That will have to do.
I step out from behind the newsstand and through my dimmed vision from the sunglasses, spot the men making a break for a car parked on the corner. It’s on the other side of the interaction from the police, and across from a two-building construction site.
Now, I know what you think I’m going to do. Stop, those robbers, right?
But, nah. The police have that under control.
What I’m more concerned about now that I’m here are all the police cars that are unattended as the police jump out of the vehicles and hit the ground, running towards the suspects. Oh, hell yeah.
As the action moves to the other side of the street, I make a break for the police cars and slide into the passenger seat of the first cruiser I see left open. I don’t have a lot of time, and this is a rare opportunity, so I move fast. I pull a flash drive from my backpack and stick it into the laptop in the seat next to mine. Already, the flash drive is installing a keylogger on the computer, so hopefully I can nab some credentials and really start hunting through police reports.
Five. Four. Just a few more seconds. Three. Two.
“I’m on it!”
I look up and see a cop running back to the cruisers. My cruiser.
“Shit,” I say, and yank the flash drive out. My arm hits up against a knob and the sirens of the car flare up. “Shit!”
I jump out of the car, and immediately, the cop spots me. “Hey!” he yells. Over where the two robbers were, the police have already subdued the pair, and attention is now being drawn back to me. Other cops look up when they hear the siren, and suddenly, I have about ten different officers staring me down. Well, that was the worst plan I’ve had today.
“Hands in the air, step away from the car!”
In a panic, I put my hands up near my head, palms out, but I’m shaking, and a new, older energy is taking over my body. One that I haven’t felt since the Facility. The wind in the intersection starts to pick up and I feel it swirling around my hands—my fingers tingling with adrenaline. With a burst of energy, I propel the wind from the palms of my hands.
There’s a crack and the roar of wind, followed by a force field extending out from where I stand, blowing away everything in my radius, razing the sidewalk clean.
Someone screams, the cops lose their footing, and I heave a breath, turning towards the skyscraper under construction. I’m cornered here. The only way to go is up.
The wind continues to howl and rip through the street and I sprint for the doors of the tower.
“Stop!”
“She has a weapon!”
It’s no longer about the robbers. It’s about me. The mutant running wild in Midtown.
My hands close around the door handle just as a shot rings out behind me. I feel burning pain, right in the bicep of my left arm, just missing my left wing. Those bastards shot me!
Boot steps, the shuffling of feet, chaos behind me. I open the door and limp inside, towards the elevator. C’mon, Willow. Like the doctors always said. Mind over matter. Mind over matter.
The elevator is taking too long, I head for the stairs, the pain in my arm refusing to subside. You just got SHOT. How do you plan to get out of this one? There’s a BULLET in you.
The stairs are a blur, I don’t remember climbing them at all, but suddenly I’m on the roof, with nowhere else to go. I can still hear the murmuring below on the street, and as I step closer to the ledge, a crowd begins to form. More police have joined the fray below.
I shut my eyes and focus on the voices below. Jessica? Is that Jessica? The voice is too mumbled to know for sure. I hear footsteps on the flights of stairs below me and I know my time is running out. There’s a steel beam that runs from the top of this skyscraper to the top of the other. The other side is not an option, though, because I hear police in that building, too.
Just as the door on the roof access door is busted open, I step out onto the beam. My arms are outstretched for balance and I carefully place one sneakered foot in front of the other.
“Stop!” one of the cops yells behind me, a woman. “You’re going to get hurt.”
Below me, I hear more sirens. Fire trucks. Let’s hear it for the boys in yellow!
I take another step onto the beam. And another. I’m out of arm’s reach now. The door on the other roof flies open and a few police officers flood out there as well. I take another step forward on the beam. Someone screams down on the street.
“Come on back!” a cop yells. “Kid—”
But I’m out of options. I stand, now, in the center of the beam, directly between the two buildings. Cops on both sides. I know what I need to do, and I don’t like it one bit.
My heart threatens to hammer out of my chest, and I turn to face the crowd below, feet planted next to each other on the beam.
Arms still outstretched, I let myself fall forward.
The screams—they’re everywhere. The ground. The police on the roof. The sirens. The wind roars in my ears and the lights around me blur.
No going back now.
I unfurl my wings and they snap me out of freefall, sending me shooting across the intersection and upward, up, up, up. The voices change below—more screams— and I rise again, the wing gathering under my wings, my lungs sipping in the cool air as my brain still tries to play catch up. The moon is out tonight, and its light guides me as I sail on streams of air towards freedom, leaving chaos behind me.
—————————————————————————–
As I continue to fly, now out by Hell’s Kitchen, I realize I need to stop. My bullet wound is really starting to hurt now that the adrenaline is starting to wear off. I lost the police and crowds when I cut through some clouds, and now I fly alone.
I still have my backpack on, and I remember that I have Jessica’s files in there. I guess I should stop while I’m here.
Mind over matter. Finish this and then get home. Have Marty help you get the bullet out.
I land on her apartment building’s roof. My smeared facepaint is still on and I pull a bottle of water out of my backpack to wash it off. After checking in my phone’s screen to make sure I got it all, I take the stairs down to her floor. It’s quiet tonight, no Malcolm in the hallway, not even an argument from the upstairs neighbor. I lift up my hoodie and see that I’ve bled through my tee-shirt underneath. Oh, well isn’t that just the cherry on top?
I knock and hear several footsteps before the door is yanked open.
“Hi,” I say, not waiting on a greeting I know won’t come. I’m in a lot of pain and I realize I shouldn’t have tried to cram this errand in. “I have police reports. A bunch. Pulled the interesting ones like you said.”
She takes the file from my hand and leafs through it. “Nice work.”
A wave of dizziness hits me and I feel my body sway a little. I steady myself and lean against the wall. I need to get that bullet out so I can heal and stop the bleeding.
“New door,” I say, nodding at it. “Looks g—” Another stab of pain hits, and my face grows flushed. I’m sweating bullets now.
“What?” Jessica looks up from my notes. “You okay? You look like shit.”
“Yeah,” I say. “I just… need to sit…” My knees give out and I collapse towards the floor, just as Jessica reaches out to steady me.
“Jesus,” she says. “What happened to you?” She helps me inside and shuts her apartment door. I lay my burning arms on her cool floor and wipe sweat from my forehead.
I don’t have enough energy to look, and I point towards my shoulder. “Got shot. Is it bad?”
“You got shot?” She drops the file in her hand and races to where I am on the floor.
“Was I doing something illegal?” I say as best I can. “You bet I was. Was it fun though? Hell yeah. Mostly.”
“This isn’t a joke, Willow!” She helps me pull the neck down on my baggy sweatshirt and get my left arm out to reveal a Pangea of blood on the left shoulder of my white tee-shirt. “Oh my God.”
“Can you—can you help me get the bullet out?” I ask.
“Are you serious? You need a doctor!”
“I can’t go to the hospital. Please. I’d do it myself, but I can’t reach.”
Jessica heaves a shaky sigh. “Where is it?”
“Follow the blood.”
She peels back my blood-soaked tee-shirt. “I see the hole.” Without any warning, she digs her fingers and yanks out the bullet.
I try not to, but I cry out and my wings shake involuntarily. I’m trying not to think about the consequences of everything that happened tonight.
“It’s okay, it’s okay, I got it,” says Jessica. “You need to—”
“I’m a fast healer,” I say, straining on each word, before passing out on her floor.
1 note
·
View note
Text
what is website malware, How it can Affect? Why Google Hates it?

All About Website Malware and Reason Why Google Hates it too much Many people come with the question “what is malware and how can it affect my website”? The expression "malware" covers a wide range of noxious programming intended to hurt a PC or arrange, and even a website. Malware can be installed on your machine without your insight, frequently through misleading links or downloads posing as something alluring or out of dread. Thus, nowadays, you must be cautious about what you click and download. Clicking new links can open you to vindictive programming and websites. This product could contain programs that scan your PC or track what keys you type, in pursuit of individual information and your passwords.
Does anybody really know "What is Website Malware"
Numerous websites experience the ill effects of malware quite frequently and more often than not it wasn't something the proprietor of the website fouled up, the site coincidentally got hacked through an open passage. Thus, be certain that you totally trust a website before clicking on it or downloading records from it.
We suggest that you just download from sources you trust, and drift over links to check the location before you click. If all else fails, utilize believed bookmarks for significant sites or program scanning expansions like McAfee for Chrome.
Can Website Malware Affect the Computer?
Numerous website proprietors are surprised with the inquiry "how do websites get infected with malware"
When a PC has been compromised by malware, digital criminals can endeavour to get to your own information by logging your keystrokes or monitoring your PC's activity. Your PC could likewise be controlled to visit websites or perform different activities without your insight. The impacts of malware run from brief irritation to finish PC crashes with the Blue Screen of Death (BSoD) to more elevated level identity robbery events. Be that as it may, its likewise basic you should realize how to find malware on your website.
The different types of malware include, but are not limited to:
Viruses
Worms
Spyware
Adware
Trojan ponies
Rootkit
Backdoors
Keyloggers
Ransomware
Redirectors
Malware can be tough to evacuate, and no single program is ensured to catch and tidy up everything, so indeed, you must be incredibly cautious about which sites you visit and what you download.
What Are Some Malware Warnings and How Can I Deal with Them?
To ensure web surfers, Google is continually working to distinguish and blacklist risky pages and domains. Numerous well-known applications (Google Search, Google Chrome, Firefox, Safari, and so forth.) utilize Google's malware database to caution their clients to avoid possibly destructive sites. The majority of blacklisted sites are in reality legitimate websites into which programmers have inserted noxious content by exposing a vulnerability and manipulating records or envelopes.
Frequently, the site proprietors are having trouble, both in cleaning up their sites, just as in removing malware warnings that truly sway their sites' traffic and notoriety.
To find out what's off with your site or some other site, you can basically counsel a Google's Safe Browsing demonstrative page. From the indicative, you first need to determine what Google precisely blacklisted. This information can assist you with narrowing down your inquiry to explicit segments of your site.
On the off chance that your site is blacklisted or set apart as "This site might be hacked" in Google's query items (SERPs), you can, for the most part, find additional insights concerning your concern in the "Security Issues" segment of Google Search Console, already Webmaster Tools. The subtleties may include site pages where Google identified malware or spam, kind of malware and instances of the vindictive code to find and expel from the documents.
How Can I Clean My Site From Malware?
When you've recognized the wellspring of the issue, you should realize how to deal with website malware. You should simply to tidy up your site and make a move to forestall re-infection. The least demanding approach to clean a site is to reinforcement the latest restore point of the web records and database, place on a testing server and begin the cleaning procedure.
During this time is the point at which you ought to make the genuinely necessary protection strides to significantly diminish re-infection or re-injection of malware.
Look for noxious documents shrouded somewhere down in directories that may look legitimate
Remove documents that look suspicious (in the event that you built up the site, at that point you will know immediately)
Remove any backdoor contents that might be lingering in organizers or parts of different documents
Before uploading the cleaned form of the website, begin changing passwords from any realized passages, for example, database login, SSH/SFTP, FTP, CMS Admin logins for WordPress, Drupal, Joomla, Magento, and so forth
If using a database or CMS like WordPress, Drupal, Joomla or Magento to give some examples, ensure you have their center forms state-of-the-art, alongside any of their expansions or plugins refreshed
Overwrite the current infected website documents and database with the new cleaned rendition
At that point change server-level passwords for your cPanel and then your domain registrar and even your Mail IDs that may have a record of the old and/or new login subtleties
Application user utilizes automated tools and can refresh vindictive content on compromised sites each day. Thus, in the event that you don't verify the site, it might be blacklisted again very soon, or may not pass the initial malware audit from Google.
It is imperative to investigate the issue and recognize the security gaps that left the website defenceless to assault. You will have a superior handle about what caused your particular issue and what ought to be done to anticipate it. Each case is distinctive as these malware bots and programmers are evolving similarly as quick as the web itself.
How to Request a Malware Review from Google?
Once you clean your site it's presently time to demand a proper audit from Google. You should be signed in to your Search Console account and on the left side, click on "Security Issues" in request to consider them to be as shown above with the malware listed.
Scroll to the bottom and check the case "I have fixed these issues" and snap the red "REQUEST A REVIEW" button to get a little spring up window.
Be sure to detail your strategies in cleaning the website inside the portrayal box and request Google to survey the solicitation as quickly as time permits. As far as we can tell, on the off chance that you or your designer has done everything right, at that point Google commonly discharges the blacklisting notice within that day or before breakfast.
NOTE* You won't get a notice from Google letting you realize the site has been discharged, so make certain to check the domain frequently. In the event that it continues for a considerable length of time with the notice still visible, attempt again.
Once no malware is discovered, Google will expel the warning from your site. These additional means are required on the off chance that you need to rapidly have your site displaying online typically again for those browsing using Google Search and Chrome, Firefox and Safari. Without manual instruction, it might take a little while before your site's status is cleared when Google makes its path back to continue indexing new sites and pages published to the web each second.
Finally, You Must Act Quickly! Malware can happen whenever, so it is significant that you are always checking your website for any issues that might be available and, all the more critically, keep your email related to your Google Search Console record to get sees as they are found. On the off chance that a website security issue was to reappear, make certain to make a move at the earliest opportunity in request to downplay your site's downtime and Google glad to show your URL to your customers and potential customers. Connecting with New York, USA based Digital marketing agency can help you in the most ideal manner in giving leeway.
Read more:- How can Paid Search Engine Marketing be an effective Strategy for B2B?
1 note
·
View note
Text
Windows 10 Preparing Security Options Stuck? Fix It Now

Windows 10 Planning Security Choices stuck issue frequently happens when the PC will stack the lock/sign on screen or the Undertaking Director. At the point when you are annoyed by this issue, you won't get to your Windows successafully. Presently, this Pen Drive Recovery software arctile can assist you with disposing of this issue.
Windows 10 Stuck on Planning Security Choices
Strategy 1: Detach the USB Gadgets
Strategy 2: Use Framework Reestablish
Strategy 3: Uninstall As of late Introduced Windows Updates
Strategy 4: Incapacitate Quick Startup
Strategy 5: Run SFC and CHKDSK
Strategy 6: Rename Programming Appropriation Organizer
Strategy 7: Reconstruct BCD
Strategy 8: Check A few Windows Administrations' Status
Technique 9: Handicap Qualification Chief Assistance
Technique 10: Reset Windows 10
On the off chance that Your Information Get Lost At last, Use Pen Drive Recovery to Reestablish Them
End
Windows 10 Planning Security Choices FAQ
Windows 10 Stuck on Planning Security Choices
Nothing is generally great, and Windows 10 is something similar. While running Windows 10, you might run over different sorts of issues.
For instance, when your PC is attempting to stack the lock screen or the sign on screen, you might observe that it is stuck on Planning Security Choices Windows 10 blue screen for quite a while. Furthermore, this issue can likewise happen when you are attempting to stack the Errand Chief.
What does Windows 10 Getting ready Security Choices stuck mean? At the point when this issue occurs, you will not be able to involve the console and mouse in any capacity except if the cycle is finished. Nonetheless, here and there, it doesn't appear to be that it will end in a brief period. Then, how to dispose of this Windows 10 blunder Getting ready Security Choices?
In this article, we sum up 10 distinct strategies which are ended up being successful. You can attempt them individually to take care of you. Obviously, in the event that you are running Windows 7/8/8.1, you can likewise attempt these answers for fix the issue.
Top 10 Methods for fixing Window 10/11 Stuck on Stacking Screen Issue
Windows 10 stuck on stacking screen? Top 10 arrangements are here to help you out of Windows 10 dark screen with stacking circle and cursor.
Strategy 1: Separate the USB Gadgets
According to a few genuine cases from the web, the associated USB gadgets like consoles, mice, and Bluetooth/Wi-Fi connectors can cause Windows 10 Getting ready Security Choices stuck issue.
Why?
Some USB gadgets have been infiltrated by keyloggers and spyware which can create the blunder issue. To address this issue, you ought to disengage all the USB gadgets from your PC and afterward reboot your PC to see whether this blunder vanishes.
Strategy 2: Use Framework Reestablish
Assuming that Windows 10 stuck on Planning Security Choices issue continues, you want to utilize different answers for take out this mistake. In the event that you have made a reestablish moment that the PC was working ordinarily, you can utilize Framework Reestablish to have an attempt.
Since the PC is unbootable, you want to go to the Windows Recuperation Climate (WinRE) to play out a framework reestablish.
Move 1: How to Enter WinRE?
1. Set up a Windows establishment plate.
In the event that you don't have one, you can go to the Microsoft Programming Download webpage to download one to an ordinary working machine and afterward make a Windows establishment medium.
2. Embed the Windows establishment plate into your PC and afterward set the PC to boot from it.
3. In the wake of entering the Introduce presently screen, click on Fix your PC. Then, you will enter WinRE.
click Fix your PC
Move 2: Play out a Framework Reestablish
1. Go to Pick a choice > Investigate > High level choices > Framework Reestablish.
2. Press Straightaway.
click Straightaway
3. Pick the reestablish point you need to utilize and press Straightaway.
press Straightaway
4. In the wake of affirming the reestablish point, press Finish. Then, at that point, adhere to the guidance to begin the framework reestablish process.
At the point when the cycle closes, reboot your PC USB Drive Recovery software see whether Planning Security Choices Windows 10 blue screen vanishes.
What Is Framework Reestablish Point and How to Make It? Look Here!
What is a framework reestablish point and how to make reestablish point Windows 10? This post will show you the responses.
#Pen Drive Data Recovery#USB Drive Data Recovery#Pen Drive Recovery#USB Drive Recovery#Pen Drive Recovery software#USB Drive Recovery software#Pen Drive Data Recovery software#USB Drive Data Recovery software
0 notes
Text
How to detect a keylogger on mac

How to detect a keylogger on mac how to#
How to detect a keylogger on mac software#
How to detect a keylogger on mac download#
How to detect a keylogger on mac mac#
If CleanMyMac X finds anything, all it takes is a press of another button to remove it.
How to detect a keylogger on mac mac#
You can use that to scan your Mac at the press of a button. CleanMyMac X has a malware removal tool that has a regularly updated database of known malicious code.
How to detect a keylogger on mac how to#
Depending on the application, you may have to pay for a full version to get rid of any malware it finds.Īnother option how to remove keylogger is to use CleanMyMac X.
How to detect a keylogger on mac download#
For example, there are several antivirus tools for Mac, like BitDefender or Avast, that you can freeload and use to scan your Mac. If the keyboard logger was installed via malware, you could get rid of it using antivirus software. However, if an employer installed it on your work Mac, you should speak to them. In the latter situation, you should attempt to remove it using the steps below. There are two possibilities if you find a keyboard logger on your Mac: that someone put it there deliberately by sitting in front of your Mac and fitting or installing it, or that you downloaded malware that contained the keyboard logger. What should I do if I find a keyboard logger? You can check for keylogger with an app called Little Snitch, which alerts you whenever a process on your Mac phone’s home and allows you to block it. This method will work for you if you know all apps that are running on your Mac. If the keyboard logger was installed by malware, it would likely send back the keystrokes log to a remote server, known as ‘phoning home’.
You should see a description of the process in the Terminal window.
Type its name without the square brackets.
Type: man – where is the process you wrote down.
Go to Applications > Utilities and launch Terminal.
Check for processes that look like they might be keyboard loggers. For example, the Spyrix Keylogger appears in Activity Monitor as skm.
Go to Applications > Utilities and double-click Activity Monitor.
If there’s no sign of a hardware keylogger, the next step is to launch Activity Monitor. If you use an external keyboard, this is likely to be plugged into your keyboard or somewhere between your keyboard and your Mac. In case you're asking yourself how to detect keylogger, the first thing to do is to check for a hardware keylogger. They are among the top 10 Mac keyloggers. Known Mac keyloggers include Aobo Mac Keylogger, Refog Keylogger, and Spyrix Keylogger for Mac. Yes, there are several keyloggers available for the Mac. They use keyloggers to discover and steal passwords or other confidential information. So it’s important to know how to protect your data and your Mac. But the danger lies in other kinds of users - hackers. Keyloggers can be used by ordinary people like parents who wish to monitor their children's computers. While there are lots of legitimate (depending on your point of view) uses of keyloggers, there are also lots of ways in which they’re used unethically and even illegally. Also, if the keylogger is equipped with a geolocation feature, it can be used to locate Mac that was stolen. An example of a keylogger that is used for good can be parental control.
How to detect a keylogger on mac software#
For some, it’s threatening malware, for others - useful software installed on Mac devices. The nature of a keylogger is dual, meaning it can be good or evil depending on how it is used. Once the keystrokes have been recorded, anyone with access to the keylogger can see what has been typed on the keyboard, including usernames, passwords, bank details, and even the content of your messages and emails. There are two types of keyloggers, software- and hardware-based, which connect to the USB port on your Mac. Keyloggers record the keystrokes typed on your Mac’s keyboard. If you’re worried that a keylogger is recording your Mac’s keyboard, there are a number of steps you can take to find out and then remove it. But to help you do it all by yourself, we’ve gathered our best ideas and solutions below.įeatures described in this article refer to the MacPaw site version of CleanMyMac X. So here's a tip for you: Download CleanMyMac to quickly solve some of the issues mentioned in this article.

0 notes
Text
Webroot Antivirus- get it now -24/7 customer support

Webroot Antivirus- get it now -24/7 customer support -If you have already purchased webroot security products and want to download visit official website webroot.com/safe.
What is “Webroot.com/safe”?
You “webroot.com/safe “ is the right page to download your webroot product. A user can download the Webroot program directly from this page without creating a Webroot account. However, creating an account is still a better option as you can log into your Webroot account and get your product anywhere and install it on any device. Also if you somehow lose your antivirus in some way, all you need to do is log in to your account and you can recover your software from that location. Account creation is given just after the top section.
How to download webroot antivirus on your Windows 10?
So let’s start I’m giving you webroot download instruction’s on my new page so, please be carefully follow these steps: Webroot Antivirus- get it now -24/7 customer support –
First, of all Start with the setup and download the software and install it at www.webroot.com/safe which you can do without a CD or DVD. All you need is a good internet connection for this purpose.
And very carefully you will find a 20 character alpha-numeric code (XXXX-XXXX-XXXX-XXXX-XXXX) which is your product key.
If you buy a retail card, you will find this unique code on the backside of the card that you need to enter.
Then Install Webroot with this Product Key by entering this unique product key to complete the installation process and clicking on the ‘Submit’ button.
Now with the Webroot.com/Setup Product Key, you can complete the installation process all by yourself. Here are some troubleshooting tips for a smooth Webroot installation.
And if the automatic download fails, you can call the helpline for help. A slow internet connection can cause problems downloading.
note- If you already have an anti-virus installed on your device, you will have to uninstall that first and remove it completely from your system.
And you make sure that the latest updates are installed on your operating system so that it is compatible with Webroot Antivirus.
What is the simple rule of the webroot installation process?
This solution addresses Webroot SecureAnywhere for Mac OS X 10.7 and higher: Webroot Antivirus- get it now -24/7 customer support –
You can install SecureAnywhere on your Mac OS X 10.7 and above. And requires an Internet connection to install its software.
After that you have to install your software:
First of all, you click this link webroot to download SecureAnywhere installer for your Mac.
After that, you double-click wsamac.dmg to open the installer.
And then you drag your Webroot SecureAnywhere icon into the Applications folder.
And you open the application folder by double-clicking on your folder and icon.
Then in your Applications folder, double-click the Webroot Secure Anywhere icon to begin activation.
After that in the first activation window, select a language from the drop-down and box and click Next.
“The most important thing – Make sure you select the desired language. Once SecureAnywhere installs, you cannot change it. “
In it, now in the first activation window, enter your keycode and click activate.
Your keycode is the 20-character license that identifies your Webroot account. If you purchased the product online, the keycode is provided in an email from Webroot. If you purchased the product in a store, the keycode is provided in the retail box. In addition, the keycode identifies whether you purchased a multi-user license, which allows you to install SecureAnywhere on up to three or five Macs.
Then in the next panel, enter your email address and click continue. (If you do not want to provide your email address, you can click Cancel to skip this step. Installation continues even if you cancel.)
If you are prompted, enter your Apple system password to confirm the installation and click OK.
After that in the next panel, you can start creating a Webroot account. You only need to create an account if you plan to use the password management feature (see Getting Started with Password Manager for more information only). Or, you can click skip and create an account later.
And if you click Create Account, your browser opens on the SecureAnywhere account creation page. Enter the required information and click Register now. For more information about account creation, see Creating a Webroot account.
Then in your next panel, you can install a Safari extension, which allows SecureAnware to tag search results as safe, suspicious, or unsafe. With this extension, SecureAnywhere tells you if a website has a reputation for spreading malware or phishing attempts. We recommended that you click on the Install Safari Extension button. (However, you can click on skip by turning on the Web Threat Shield and installing it later, as described in the Web Threat Shield setting.)
You then click on the install button, in the Safari dialog.
After that, if you have full or Internet Security Plus versions, Safari asks if you want to install the “Webroot” extension, which includes password management functions (see Getting Started with Password Manager for more information). If you want to use password management features then click on install.
And a dialog opens when you configure your password manager in your browser.
and If you installed both extensions, two Webroot icons appear in the browser toolbar. The example below shows how the icons appear in Safari and Chrome; the icons in Firefox look slightly different. (You can hover your mouse over the icons for pop-up descriptions.)
a. This icon indicates that the Web Threat shield is enabled. See Using Web Threat protection.
b. And then this icon shows you that password management features are enabled. When you install the extension for the first time it goes gray-out. If you have already created an account, you can click on the icon and enter your login credentials to start using password management. See Getting Started with Password Manager.
And when the activation successful screen opens, click the scan button.
Webroot Antivirus starts scanning your Mac for viruses, spyware, and other potential threats. If it detects threats during the scan, it prompts you to take the items into quarantine. And in this quarantine, items are rendered passively and then can no longer harm your system or steal data.
In the Scan Full window, you close it and click on.
For more information, you should visit our web page and get information. And in case of any problem, contact us on the toll-free number given.
How can webroot.com/safe help me?
Webroot support specialists can lend you their hands to download, install and update Webroot Spy Sweeper Antivirus on your system. We can also correct all errors that can crop up when installing and configuring Webroot Antivirus on your PC.
We can help you detect and remove malicious threats, malware, and spyware by doing a quick scan of all files and folders. With our robust technology, we can delete suspicious programs and infected files from your system. Our antivirus specialists can clean up all online threats, including Trojans, rootkits, keyloggers, and worms. We can optimize the speed and efficiency of your computer and also prevent it from becoming sluggish.
And now just give us the green light to remotely access your computer via the Internet and our certified technicians can protect you from identity theft and prevent unauthorized users from accessing your computer and personal data.
Tips for the successful install before reaching: Webroot Antivirus- get it now -24/7 customer support –
For a successful install of webroot safety in a computer, a user needs to ensure that he does not have any other antivirus already on the computer. Users step:
First of all, the open control panel on your computer. allocate programs and features section inside the control panel home.
In programs and features section check the complete list of the installed program.
Find any other antivirus program.
If you found any double click on it. In order to remove it.
Now restart your computer.
Frequently Asked Questions :
Is Webroot good antivirus software?
Protection Features. Like most modern antivirus programs, webroot secures anywhere Antivirus detects malware by comparing suspicious programs found on your computer with an enormous database of known malware. In Webroot’s case, that database is not on your PC, but in the cloud.
WHAT IS WEBROOT KEY CODE?
A webroot key code is 20 characters alphanumeric string which is situated at the back of the webroot retail card. We should peel it off gently.
WHY I USE WEBROOT?
Webroot has blocked malware and other bad stuff from infecting a computer. The few times I’ve needed tech support due to my computer inexperience.
How do I redeem my Webroot code?
Open your Webroot program and click the gear icon next to My Account. Enter your keycode in the Activate a New Keycode field, then click Activate. If a scan begins automatically, allow it to complete.
What is Webroot Software?
BLOCKS VIRUSES & MALWARE: Cloud-based antivirus software from Webroot provides comprehensive internet security protection for your PC or Mac without slowing you down.
IDENTITY THEFT PREVENTION: Defends you against identity theft by protecting private information like usernames, passwords, account numbers, and more.
Does Webroot scan for malware?
Antivirus software such as Webroot SecureAnywhere Antivirus frustrates malware in a couple of ways.
It scans data and blocks viruses that it detects. And it removes malware that is already lodged in a computer.
You can tell it to scan your PC according to a schedule that you select.
Does Webroot have a free version?
Webroot’s SecureAnywhere Anti-Virus protects your system against all types of malware threats.
This version offers you a 15-day free trial to evaluate the software and determine how well it suits your needs.
1 note
·
View note
Text
Spytech keylogger for mac vs

#Spytech keylogger for mac vs for free#
#Spytech keylogger for mac vs how to#
#Spytech keylogger for mac vs software#
#Spytech keylogger for mac vs download#
That’s what Dell Technologies Advisors do. To succeed, you need someone to guide you through. Sometimes it feels like the world is throwing everything it has at you. Operating system updates play a part in ensuring your computer is protected from the latest dangerous tricks cybercriminals play. Cybercriminals are always looking for unprotected devices on public networks in hopes of infecting them with malware.Īnd, of course, you need to keep your computer updated. Never connect to public Wi-Fi without the protection of a virtual private network (VPN). Next, protect your devices from snoops and spies. They could be malicious and infect your device with keylogging malware. Also, don’t open attachments found in messages, either. Scammers are so good at spoofing messages and websites these days you never know if it’s real or fake.Īs always, the best way to get to an official website is to type the address directly into your browser. Just follow some simple safety precautions, so you don’t become the next phishing victim.įirst, always be cautious with links found in unsolicited emails and text messages. Since keyloggers can be installed on your device through phishing attacks, you can avoid the problem before it even begins.
#Spytech keylogger for mac vs download#
It works for Windows computers and you can get the freeload here or by clicking the button below.
#Spytech keylogger for mac vs software#
Ghostpress is an anti-keylogging software that prevents malicious software from capturing your keyboard presses. If you don’t feel comfortable going through this process on your own, a freeload can help. Uninstall suspicious programs that may be a keylogger. You will see a list of all programs that are installed on your computer. Next, select Programs and then Uninstall a Program. Click on the Control Panel app when it appears. A simple way to do this is to type “control panel” in the search box found in the lower-left corner of your PC. Go to your Control Panel as if you are going to uninstall a program. This will help you weed through all of the apps on your computer. You can group your applications by clicking the View option in the menu and then Use Groups. Select your Applications folder and review installed programs. Go to your desktop and click Finder in the upper left and open a new finder window.
#Spytech keylogger for mac vs how to#
Here’s how to find installed programs for both Mac and PC: Checking for installed programs on a Mac Some other known keylogging programs to watch for include DanuSoft, Refog, and Spytech. Obviously, anything with the word keylogger in the title is a dead giveaway. If you don’t recognize the name of a program, do a Google search to find out what it is. So, what are you looking for? Pretty much anything unfamiliar or suspicious. To do this, you’ll need to check your list of installed programs. However, since some keyloggers are constantly being updated with new ways to outsmart detection, you may want to do some digging on your own. Also, make sure your operating system is updated regularly, so you get security patches that help block these types of threats. Most trustworthy antivirus programs automatically check for keyloggers, which is why it’s crucial to have one protecting all of your devices. Keyloggers can be challenging to find but not impossible.
#Spytech keylogger for mac vs for free#
Call an advisor at 877-ASK-DELL or go to for free expert support. That could include account credentials and other sensitive information. The programs are also used for shadier reasons, like keeping tabs on a significant other or looking to rip people off by cybercriminals.īecause once the program is installed on your device, a crook can record everything that you type. There are legitimate uses for keyloggers, such as parents who want to monitor their children’s internet activity or (like it or not) by employers making sure workers are productive. Another sneaky way thieves can rip you off is through a keylogger, a program secretly installed on your device to record keystrokes. One example comes in the form of malicious apps that are designed to run adware. Sometimes, their schemes run behind the scenes on your device and you may never know what’s going on. Criminals looking to rip you off never stop coming up with clever new ways to do it.

0 notes